DAG TECH CxO

With DAG Tech’s CxO services, an experienced subject matter expert is available to you for a fraction of the cost.
Delivering Outcome-Oriented C-Level Expertise
In today’s landscape, technology leadership and proficiency are indispensable for the prosperity, expansion, security, and compliance of any organization.
Whether it’s an enterprise or a smaller entity, dedicated technology roles are essential for harnessing technology’s potential, safeguarding communications and valuable data, and upholding industry standards.
DAG Tech’s CxO services offer exceptional value and seamlessly integrate subject matter experts to drive impactful results.
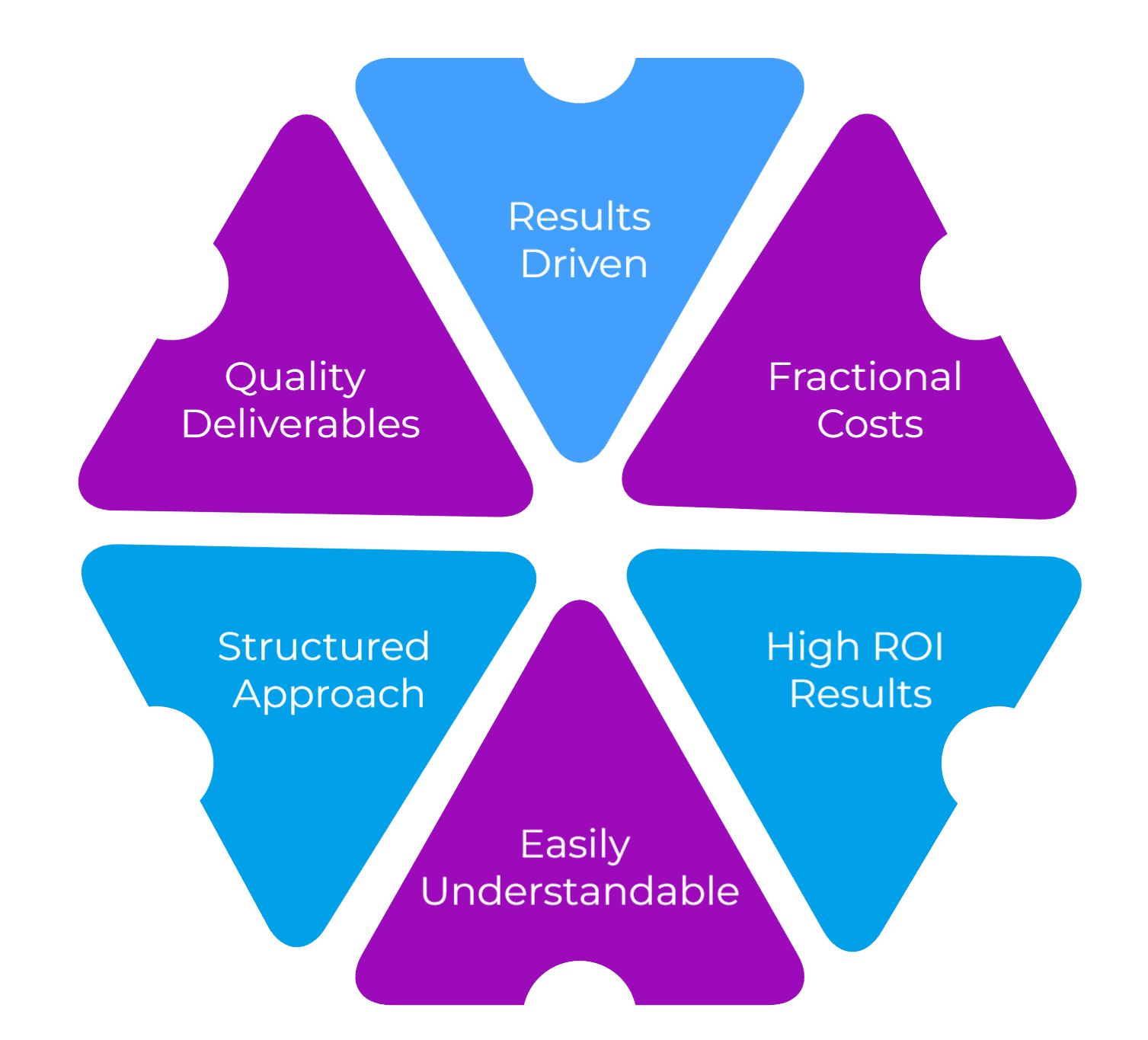
DAG Tech CxO benefits
How do DAG Tech CxO services work?
Initiation
To initiate our CxO services, we discover your organization’s objectives. With these findings, we build out a CxO program timeline, with the proper experts, to study and accomplish specific deliverables.
Deliverables
We deliver reports and documents in formats that are comprehensible to executives, board members, and all relevant stakeholders. These formats provide valuable insights, suggested solutions, and actionable strategies. Strategies may encompass technology projects, migrations, consolidations, footprint reduction, the introduction of new services, enhanced security measures, compliance adherence techniques, and the creation of new policies.
Engagement
Our C-class experts are leading technologists, security experts, and compliance specialists with vast experience and track records of proven results. DAG Tech CxO is available as ongoing plans or as one-time projects. All services are provided by our world-class team.
Definitions
C-level services are often referred to as:
- Fractional – fractional in time requirements and cost
- Outsourced – hired externally, as opposed to in-house
- Virtual – performs functions via video, email, and phone

